Avalanche Effect in Cryptography
The fascinating phenomenon known as the Avalanche Effect plays a pivotal role in safeguarding sensitive data in cybersecurity and encryption.
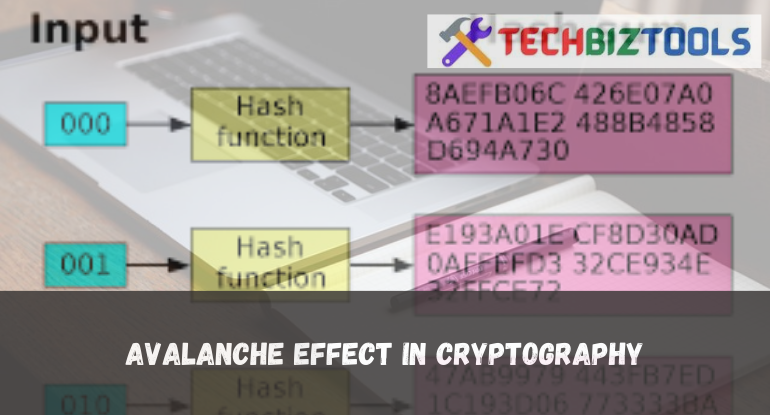
Imagine a scenario where the slightest change in input results in a significantly altered output—this is the essence of the Avalanche Effect in cryptography.
It stands as a cornerstone in ensuring the robustness of cryptographic algorithms, fortifying them against malicious attacks and ensuring the confidentiality, integrity, and authenticity of information in our digital world.
Let's delve deeper into this intricate yet crucial concept that underpins the security of our online transactions, communications, and data storage.
Understanding the Avalanche Effect
The Avalanche Effect within cryptography lies at the heart of its transformative capacity. It's essentially the idea that the smallest change in input a tweak to the plaintext or cryptographic key triggers a drastically different output.
Picture it as a cascade effect where even the tiniest alteration ripples through the entire encryption process, completely reshaping the resulting ciphertext.
This concept acts as a powerful defense mechanism against those attempting to crack encrypted information. Its purpose is to obscure any connection between the original message and its encrypted form.
This intentional convolution makes it incredibly challenging for adversaries to discern patterns or extract any meaningful data from the encrypted output.
In simpler terms, it's like shuffling a deck of cards with a minor change—a single card moved or shuffled differently causes a completely different sequence. This disruption is what makes encrypted data so formidable to decode and ensures the security of sensitive information in the digital realm.
The Role of Avalanche Effect in Cryptography
The Avalanche Effect stands as a stalwart guardian within cryptography, offering a critical shield against a spectrum of potential attacks. Its significance is vividly evident in cryptographic algorithms like the Advanced Encryption Standard (AES), a linchpin in global information security.
AES operates meticulously, orchestrating intricate sequences of substitutions, permutations, and bitwise manipulations. Even the smallest tweak in the input sets off a chain reaction, transforming the output in a domino effect, creating layers of complexity that veil the ciphertext.
The roles of Avalance Avalanche Effect in Cryptography:
#1. Avalanche Effect's Guardian Role: The Avalanche Effect emerges as a stalwart defender within the realm of cryptography. It acts as a crucial defense mechanism, forming a shield against a diverse array of potential attacks that aim to compromise sensitive information.
#2. Illustration through AES: The significance of the Avalanche Effect becomes strikingly apparent in the workings of widely used cryptographic algorithms like the Advanced Encryption Standard (AES).
AES operates with meticulous precision, executing intricate sequences involving substitutions, permutations, and bitwise manipulations.
#3. Domino Effect of Input Changes: Even the most minuscule alteration in the input initiates a cascade of transformations in AES. This domino effect alters the output in a complex manner, creating multiple layers of intricacy that obscure the resulting ciphertext.
#4. Hash Functions and Data Integrity: Hash functions, pivotal for maintaining data integrity and validating digital signatures, heavily rely on the Avalanche Effect. These functions produce fixed-length outputs (hashes) from inputs of varying lengths.
#5. Seismic Impact on Hash Values: Within hash functions, any modification to the input—regardless of its size—causes a significant upheaval in the resulting hash value. This fundamental behavior ensures the integrity and authenticity of the data, making it highly resistant to tampering.
#6. Unsung Hero of Cryptography: In the broader context of cryptography, the Avalanche Effect assumes the role of an unsung hero.
It fortifies the protective barriers that safeguard our most sensitive information, reinforcing the foundational structure upon which secure digital communications rely.
#7. Silent Strength in Safeguarding Information: Its silent but powerful contribution is felt across various layers of encryption and security protocols, ensuring that encrypted data remains resilient against malicious attempts to decipher or alter it.
#8. Essential Foundation for Secure Communication: Ultimately, the Avalanche Effect plays a foundational role in ensuring secure digital communication.
Its ability to obscure, transform, and authenticate data stands as a cornerstone in upholding the confidentiality and integrity of information transmitted across digital channels.
Unveiling the Mechanisms
Unraveling the inner workings of the avalanche effect unveils a world of intricate mathematical maneuvers within cryptographic algorithms. To achieve this phenomenon, sophisticated techniques like confusion and diffusion come into play as indispensable tools.
Confusion aims to tangle the relationship between plaintext and ciphertext, while diffusion ensures that even the slightest alteration in input triggers a cascade effect throughout the entire output.
This dynamic process renders encrypted data incredibly sensitive to any variations in the original message, contributing to the robustness of cryptographic security.
However, while the avalanche effect stands as a stalwart defense mechanism, it's crucial to recognize that the security of cryptographic systems transcends this singular property.
Safeguarding against side-channel attacks, addressing potential implementation flaws, and fortifying defenses against cryptanalysis are equally paramount in bolstering the resilience and strength of encryption methods.
The avalanche effect is just one piece of a multifaceted puzzle that constitutes the broader landscape of cryptographic security.
The Ongoing Quest for Secure Systems
The pursuit of stronger cryptographic systems persists in a era marked by rapid technological evolution.
Researchers and cryptographers continually refine algorithms, subject them to rigorous testing, and innovate novel approaches to fortify encryption methods against evolving threats.
#1. Continuous Evolution: In an era defined by rapid technological advancements, the quest for fortified cryptographic systems remains ongoing. This pursuit involves a perpetual cycle of evolution, adaptation, and enhancement.
#2. Research and Refinement: Cryptographers and researchers are at the forefront, constantly refining existing algorithms. Through meticulous analysis and rigorous testing, they strive to identify vulnerabilities and bolster the resilience of encryption methods.
#3. Innovation and Novel Approaches: The landscape of cryptography thrives on innovation. Cryptographers explore novel approaches, leveraging cutting-edge technologies and fresh perspectives to fortify systems against emerging threats.
#4. Adaptation to Evolving Threats: The dynamic nature of cybersecurity demands constant vigilance. Cryptographic systems must adapt to and anticipate evolving threats, staying one step ahead of potential vulnerabilities and attacks.
#5. Rigorous Testing and Validation: Before deployment, cryptographic systems undergo extensive testing and validation processes. This ensures their efficacy, resilience, and ability to withstand various forms of attacks.
#6. Collaborative Efforts: The quest for secure systems is a collaborative endeavor. Researchers, cryptographers, and cybersecurity experts worldwide collaborate, sharing insights and knowledge to collectively strengthen encryption methods.
#7. Balancing Efficiency and Security: Innovations aim not only for heightened security but also for efficiency. Striking a balance between robust security measures and operational efficiency is crucial in deploying effective cryptographic systems.
#8. Anticipating Future Challenges: Forward-thinking approaches involve anticipating future challenges. Cryptographers proactively analyze potential future threats, preparing cryptographic systems to withstand and mitigate these challenges.
#9. User Education and Awareness: In tandem with technological advancements, educating users about the importance of encryption and cybersecurity plays a pivotal role. Awareness empowers individuals to play an active role in maintaining secure systems.
#10. Regulatory Compliance and Standards: Adherence to regulatory standards and compliance frameworks ensures a baseline level of security across industries. It sets benchmarks for encryption methods, fostering a more secure digital environment.
Conclusion
The avalanche effect stands as an indispensable cornerstone of cryptographic security, amplifying the potency of encryption algorithms against potential breaches.
Its ability to amplify the repercussions of input alterations on the output ensures the confidentiality and integrity of sensitive information, serving as the bedrock of secure digital communication.
As the digital landscape evolves and threats become more sophisticated, the continual refinement and advancement of cryptographic techniques remain imperative.
The perpetual quest for fortified encryption mechanisms and heightened security measures remain at the forefront, safeguarding the integrity and privacy of data in our increasingly interconnected world.